Advanced Information Security and Privacy Protection

Goals and KPIs
- 2030 Goal
- Establish and operate security infrastructure appropriate for social infrastructure
- 2024 Goal
- Build information security that is positioned as an important management function for the entire Chatwork Group
- 2030 KPIs
-
- Under the supervision of the CEO, formulate security strategies in response to conditions in society and business strategies related to information security, and enhance security management throughout the entire company
- Establish and operate an independent audit system to monitor security functions
- Acquire and operate under SOC2, an international security certification
- Major security incidents: 0
- 2024 KPIs
-
- Enhance PSIRT/CSIRT system
- Optimized security training program participation rate (development, corporate): 100% of relevant staff
- Implement security measures in the software supply chain
- Implement SAST/DAST for automatic early vulnerability detection
- Major security incidents: 0
*1 SOC2: Service Organization Control Type 2, a cybersecurity compliance framework developed by the Association of International Certified Professional Accountants (AICPA)
*2 PSIRT: Product Security Incident Response Team, an organization that improves the level of security and responds to incidents for products and services manufactured and developed in-house; CSIRT: Computer Security Incident Response Team, an organization that responds when an incident occurs that is perceived as a security problem
*3 SAST: Static Application Security Testing, analyzing source code to detect vulnerabilities that make an organization's applications vulnerable to attack; DAST: Dynamic Application Security Testing, detecting application vulnerabilities by simulating external attacks while the application is running
Approach and System
Approach to Information Security
We develop and provide cloud-based business chat services that streamline and revitalize business to our customers, exceeding 386,000 companies*1 with 1,053,000 DAUs*2. We are entrusted with important information assets and confidential information by our customers.
We have positioned information security as our most important management issue as the reliable protection of this information is a prerequisite for business continuity. We established our "Basic Policy on Information Security" in January 2013 and are working to ensure information security throughout the company.
View this page for the "Basic Policy on Information Security"
*1 As of the end of December 2022
*2 Median number of Daily Active Users for weekdays (excluding Saturdays/Sundays/holidays) as of the end of December 2022
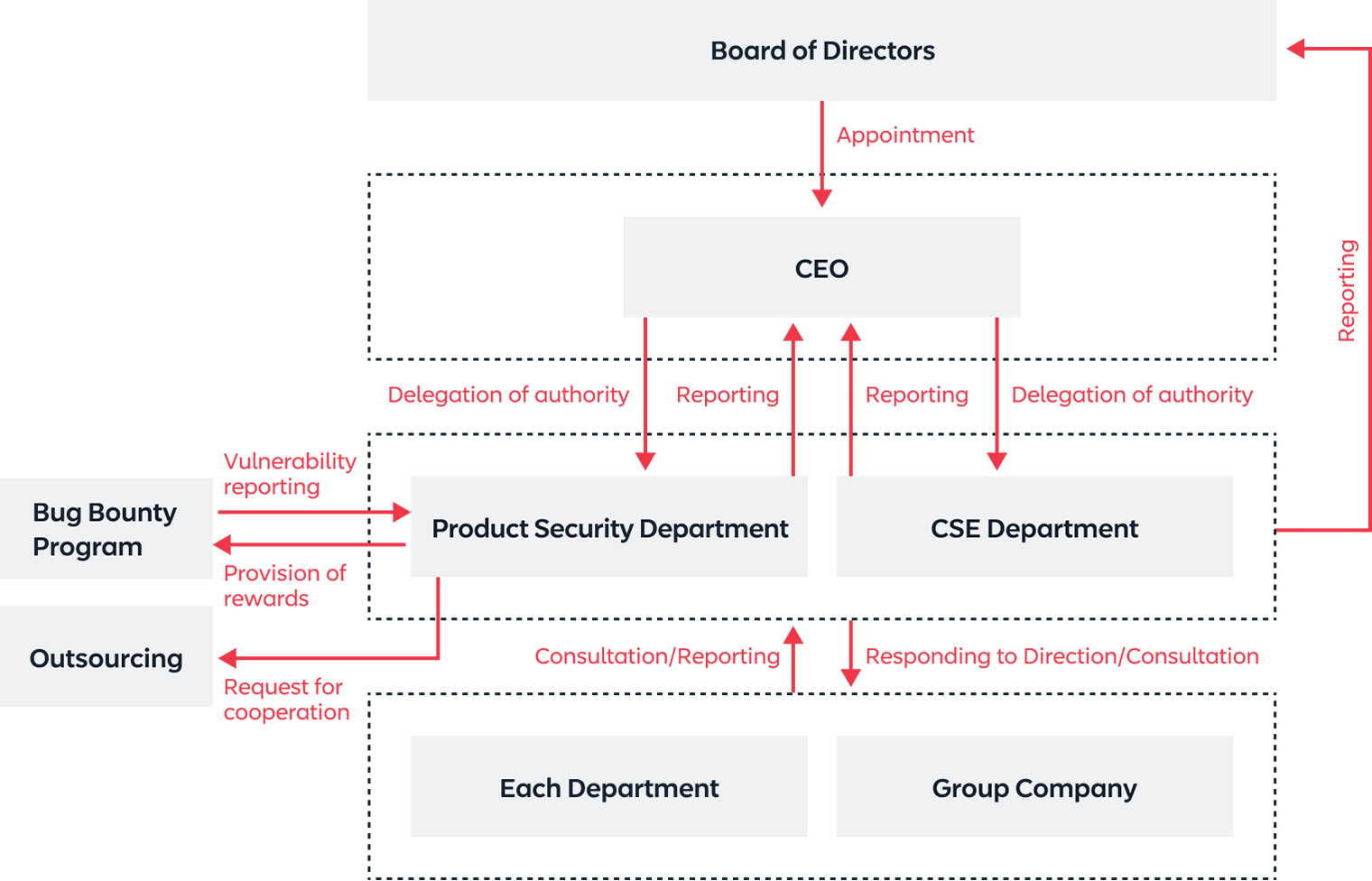
Information Security Structure
We have established an information security structure headed by our CEO. The CSE Department*1 of the Corporate Division manages information security for our entire Group's information systems, and the Product Security Department of the Product Division manages information security for the products and services we develop.
We have also appointed CISSP*2 certified personnel who possess advanced expertise in information security to respond to the changing security environment.
*1 CSE Department: Corporate Solution Engineering Department
*2 CISSP: An internationally renowned certification for information security professionals accredited by the International Information Systems Security Certification Consortium
Information Security Structure Chart
Chatwork's Main Initiatives
Initiatives to Ensure Information Security
Our initiatives to ensure information security are as follows.
1) Acquisition of International Certifications for Information Security
We operate our systems in accordance with strict security standards. All operations of Chatwork Co., Ltd. and Chatwork Storage Technologies Co., Ltd. have been audited by third party organizations. Through this process, we have acquired the ISO/IEC 27001:2013 (JIS Q 27001:2014)*1 international certification standard for information security; ISO/IEC 27017:2015*2 international certification standard applicable to the provision and use of cloud services; and the ISO/IEC 27701:2019 international certification standard for the appropriate protection of personal and related privacy information.
*1 ISO/IEC 27001:2013 (JIS Q 27001:2014): International standard for Information Security Management Systems (ISMS)
*2 ISO/IEC 27017:2015: Guideline standard for information security management measures for cloud services
ISMS Certification Acquisition Status
| Certification Name | Scope | Date of Acquisition |
|---|---|---|
| ISO/IEC 27001:2013 (JIS Q 27001:2014) | Chatwork Co., Ltd. and Chatwork Storage Technologies Co., Ltd. | #1: March 21, 2013 #10: March 23, 2022 |
| ISO/IEC 27017:2015 | Chatwork Co., Ltd. and Chatwork Storage Technologies Co., Ltd. | #1: April 10, 2018 #5: April 26, 2022 |
Acquired Certification Standards for Information Security

2) Measures Against External Attacks
The environment surrounding information security is changing rapidly. As a result, the risk of information leakage is rising each year due to increasingly sophisticated cyber-attacks and other external attacks. To respond to this risk, we are working on security measures from both product development and corporate management perspectives.
In terms of product development, we are implementing measures such as preventing and blocking unauthorized access, introducing WAF*, managing vulnerabilities to evaluate and confirm those that exist in middleware and libraries used for development, conducting security training to ensure secure development, and carrying out periodic assessments using an external security specialist company. We have also established a Product Security Department dedicated to product security measures, and have established and operate a security consultation desk and security risk reporting form where employees can consult and report on information security. Furthermore, we have implemented a "Bug Bounty Program," an institutionalized system for the discovery of vulnerabilities by external bug hunters with high technical skills that offers rewards upon discovery. We are also continuously working on developing secure products through measures such as regularly implementing risk management inventories, in which critical risks are evaluated and identified from risk incidents identified through security risk reporting forms and other means, and countermeasures are discussed.
In terms of corporate security, we are enhancing security measures at endpoints, such as the end information devices of executives and employees.
*WAF: Web Application Firewall, a security measure to protect web applications from unauthorized access, such as by blocking attacks
Primary Measures Against External Attacks
| Initiative | Overview | Frequency |
|---|---|---|
| Operation of bug bounty program | Receive vulnerability reports on applications from bug hunters and use them to enhance security | As appropriate |
| Vulnerability assessment by security vendor | Conduct annual vulnerability assessments by security vendors to enhance application security | Once/year |
| Security consultation desk | A security consultation service where developers can consult about implementation from the design stages to prevent vulnerabilities from being embedded in applications; also operates as a place where developers can easily report security incidents or the possibility of such incidents | As appropriate |
3) Measures to Prevent Internal Information Leaks
When developing products, we conduct reviews to prevent information leaks during development and have built systems whereby only the minimum necessary personnel can access the minimum necessary information to prevent unauthorized access and tempering. In addition, we carefully store important data including service access, usage, and data communication history (logs) for service maintenance and security measures, building and operating systems to monitor access to information systems. We regularly check whether these systems are being operated properly and conduct internal audits. We also take measures to prevent information leakage from those who have left the company.
In terms of ensuring corporate security, we provide information security education to all employees, set minimum access privileges for important information, manage system accounts, and store system logs. We also centrally manage the security settings of laptop computers and other terminal devices, and have introduced MDM*, which deletes all data in the event of loss, to prevent information leakage. In addition, we manage the status of the personal information entrusted to third parties and conduct security checks.
*MDM: A method to manage system settings and other aspects of terminal devices such as smartphones and laptops used for business in an integrated and efficient manner. It also refers to the software and information systems that enable this.
Primary Measures Against Internal Information Leaks
| Initiative | Overview | Frequency |
|---|---|---|
| Implementation of training for executives and employees |
|
Upon entering company, once/year |
| System account management with minimum authorization for critical information assets |
|
As necessary |
| Implementation of MDM terminal management |
|
As necessary |
4) Other Initiatives to Improve Information Security
As the risk of information leaks increases, there are limits to the measures that can be taken by individual companies. Because of this, in October 2022, we established the "SaaS Security Community" in collaboration with SaaS providers as a forum for companies that develop and operate SaaS services for BtoB to exchange information on security measures. We did this to strengthen security measures through collaboration with companies that offer similar services. The community, currently consisting of 12 companies, encourages the exchange of information and vulnerability assessments to strengthen security measures.
Privacy Protection
Our Privacy Protection Approach and Efforts
It is critical to ensure that the private information entrusted to us is properly protected and managed in accordance with the information protection regulations of each country and region in order to provide convenient and reliable IT services to all of our users.
Therefore, we have established a privacy protection policy and regularly provide training to all relevant executives and employees to ensure compliance with this policy. In addition, we acquired the ISO 27701* international certification for privacy protection in April 2022, and are working to enhance our management.
View this page for details on our privacy policy.
*ISO/IEC 27701:2019: An international standard established in 2019 and positioned as an add-on (extension) standard to ISO/IEC 27001 and ISO/IEC 27002. In addition to requirements for ISMS, it specifies requirements and guidelines for protecting privacy that may be affected by the processing of personal information.

Reproduction, duplication, or alteration of this image is prohibited
Related Key Issues
-

Ensuring Reliable Quality as Business Infrastructure
-

Conducting Sustainability Management to Achieve Corporate Philosophy
-

Achieving Corporate Governance that Drives Corporate Value Enhancement
-

Conducting Business Activities with Integrity for All Stakeholders
-

Becoming a Trustworthy Brand and Enhancing Engagement
-

Diversity Management to Achieve New Value Creation

